Keylogger's and RAT's nowadays are everybody's problem across the internet. Hackers use keyloggers to hack the email passwords of the victim which they receive in the form of emails or text files on their respective FTP servers. They spread their keyloggers with the help of cracks, keygen's or patches of popular software's or simply through hack tools. So friends, today i will teach you how to reverse engineer the keylogger or RAT to hack the hackers FTP server or email password.
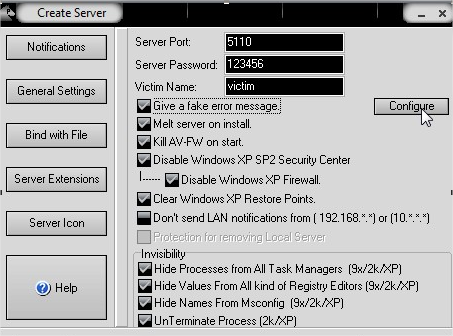
Most of hackers thinks that they are too smart, so what they do bind their keylogger or Rat servers with popular programs and when user open that their system got infected and hence what ever they type is get recorded and sent to hacker.
Now all keyloggers sent data to hacker in regular intervals (usually every 5 to 10 minutes) by using below to ways:
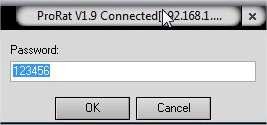
1. Using the Emails : where hacker configures his email ID and password while creating the server. Keylogger records the key strokes in a temp file and sends it to the hacker in form of emails. But this has a limit as most free email servers like Gmail or Yahoo or Hotmail has limit of 500 composed and received mails. So most hackers use the second method.
2. FTP server : While creating the keylogger server, hacker configure their FTP server, where they receive the logs of key strokes in the form of text file( usally labeled on the basis of current system time stamp). Hackers keylogger server uploads the files to FTP server after every few minutes interval.
So friends, here the actual trick or loophole in above technique lies. If we monitor the everything coming in and going out of our Ethernet card or Wireless then we can detect that what is going out of our system. Its nothing but just monitoring your your system's traffic, where its going and from where its coming. You can use any of the tool that monitor the packet flow of your Ethernet or wireless card.
ok...ok.. let me tell you my favorite tool for doing the same. I love Wireshark because its simply superb.
Wireshark is a very famous network scanning hack tool which is used by hackers or network forensic experts to monitor the packet flow of their network cards like Ethernet or WLAN. It records the each and every packet coming and going out of your system's Network card. Now you all must be thinking wth is this Packet. Packet is nothing but just a bunch of bits(data in form of 0 & 1) usually 32bit or 64bit. In network terminology, data is termed as packet which can be either TCP or UDP( both contains the header n other stuff accordingly).
So friends, whenever you feel anything suspicious in your system like your system is compromised or you are infected from a keylogger or RAT or simply you want to test a hack tool and you are not aware that hack tool is safe to use or not. Just follow the below procedure to reverse engineer these noob hacking tools.
Note: Every keylogger or RAT sends the logs to hacker's FTP server or email account after few minutes interval( when you are connected to internet) but some novice keyloggers even tries to send data while you are offline and hence the data sending keep on failing. In some situations it displays warning message and in some situations you PC gets hanged or SVHOST service CPU usage increases. But nothing matters whether it sends logs online or offline, the only thing matter is time period, after what interval it sends data.
Steps to Hack or reverse engineer the Hacker's Keylogger server password:
1. First of all download and install the wireshark. You can easily get this using by Googling it.
Note: While Wireshark is getting installed, ensure that it installs the Winpcap with it other it won't work properly.
2. Now go to the Capture button in the top menu of the Wireshark as shown below and select the interface( means your network card which can be Ethernet or WLAN).
3. Now it will start capturing the packets through that Network card. What you have to do is just keep capturing the records for atleast 20 - 30 minutes for getting the best results. After 20- 30 minutes, again go to capture and stop capturing the packets.
4. Now you need to filter your results, for this Go to the filter box and type FTP and SMTP one by one. Note: if you get records for FTP then hacker has used FTP server and if you didn't got FTP that means hacker has used SMTP, so give SMTP in Filter box.
5. As you scroll down you will find the “FTP username” and “Password” for victims ftp account in case FTP server is used. And if hacker has used SMTP then you will find "email address" and its "password" that hacker has used to create keylogger.
6. That's all my friends. Isn't that too easy.