SMS Gateway Linux
~How to Setup Gammu~
Gammu
Kebutuhan
1. Laptop/Komputer
2. OS Linux
3. Koneksi Internet (Untuk instalasi)
4. Modem
5. Kartu Perdana (Indosat, Telkomsel, Xl, dll)
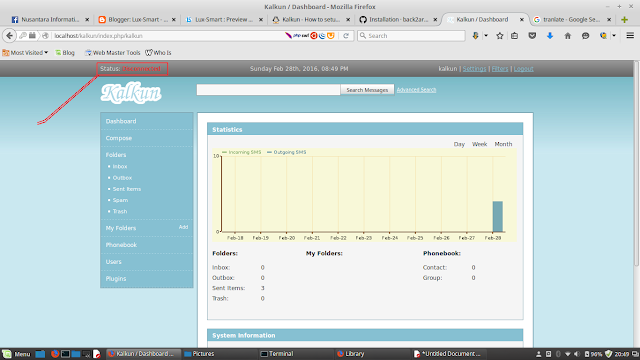
Disini, penulis menggunakan OS Linux (Linux Mint 17.3 Cinnamon 64-bit). Penulis disini nanti akan menggunakan Kalkun untuk Management SMS-nya.
Langkah-langkah Instalasi dan Konfigurasi Gammu
1. Instal Gammu
- Kemudian Connect-Disconnect Koneksi 'Mobile Broadband' pastikan lampu LED warna biru pada Modem hidup.
- Stop service gammu-smsd.
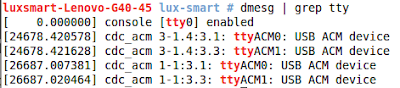
-Silahkan cek device USB yang sudah terhubung ke Laptop/Komputer.
Berarti lokasi USB Modem yang terhubung ke Laptop berada di /dev/ttyACM0.
Pengalaman menggunakan device Modem yang berbeda, contohnya: Wavecom Fastrack M1306B biasanya diminta untuk Gammu-config dahulu:

Lebih jelasnya silahkan baca disini.
2. Konfigurasi Gammu koneksi ke Kalkun.
a). Silahkan edit file gammu-smsdrc
Simpan
b). Silahkan dicoba untuk cek Pulsa dulu menggunakan perintah:

Silahkan baca tutorial : SMS Gateway How to Install Kalkun
Oke... Tinggal Testing Kirim Pesan....
Penulis telah menguji konfigurasi diatas, alhamdulillah berjalan dengan baik.
Untuk teknik lanjutan, silahkan anda kembangkan sendiri.
Untuk Troubleshooting-nya silahkan chatting aja via BBM atau Komentar dibawah... Terimakasih...
Semoga bermanfaat...
Read more
~How to Setup Gammu~
Gammu
Kalau bicara tentang SMS Gateway, ini salah satu software Engine-nya. Gammu ini sebagai SMS daemon (gammu-smsd) yang berfungsi untuk mengirim dan menerima pesan dari Phone/modem.
Kebutuhan
1. Laptop/Komputer
2. OS Linux
3. Koneksi Internet (Untuk instalasi)
4. Modem
5. Kartu Perdana (Indosat, Telkomsel, Xl, dll)
Disini, penulis menggunakan OS Linux (Linux Mint 17.3 Cinnamon 64-bit). Penulis disini nanti akan menggunakan Kalkun untuk Management SMS-nya.
Langkah-langkah Instalasi dan Konfigurasi Gammu
1. Instal Gammu
# apt-get install gammu gammu-smsd- Setelah instalasi silahkan tancapkan modem ke Laptop/Komputer.
- Kemudian Connect-Disconnect Koneksi 'Mobile Broadband' pastikan lampu LED warna biru pada Modem hidup.
- Stop service gammu-smsd.
# service gammu-smsd stop- Cek status service Gammu.
# service gammu-smsd status
-Silahkan cek device USB yang sudah terhubung ke Laptop/Komputer.
# dmesg | greb tty
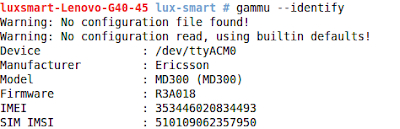
# gammu --identify
Berarti lokasi USB Modem yang terhubung ke Laptop berada di /dev/ttyACM0.
Pengalaman menggunakan device Modem yang berbeda, contohnya: Wavecom Fastrack M1306B biasanya diminta untuk Gammu-config dahulu:
# gammu-config
Lebih jelasnya silahkan baca disini.
2. Konfigurasi Gammu koneksi ke Kalkun.
a). Silahkan edit file gammu-smsdrc
# nano /etc/gammu-smsdrc
#SesuaikanVersi aslinya:
[gammu]
port = /dev/ttyACM0
connection = at
#Sesuaikan
[smsd]
PIN= ''
runonreceive = /var/www/html/kalkun/scripts/daemon.sh
logfile = /var/log/gammu.log
DeliveryReport = sms
# Increase for debugging information
debuglevel = 1
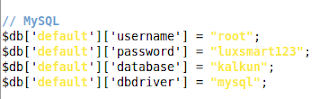
#Tambahkan Koneksi MySQL, sesuaikan dengan user, password, dan database anda.
service = sql
driver = native_mysql
database = kalkun
user = root
password = luxsmart123
pc = localhost
Simpan
b). Silahkan dicoba untuk cek Pulsa dulu menggunakan perintah:
# gammu --getussd *888#

c). Oke, silahkan aktifkan service Gammu-nya supaya dapat mengirim dan menerima pesan.
# service gammu-smsd startDisini saya menggunakan software Kalkun untuk Management SMS-nya.
Silahkan baca tutorial : SMS Gateway How to Install Kalkun
Oke... Tinggal Testing Kirim Pesan....
Penulis telah menguji konfigurasi diatas, alhamdulillah berjalan dengan baik.
Untuk teknik lanjutan, silahkan anda kembangkan sendiri.
Untuk Troubleshooting-nya silahkan chatting aja via BBM atau Komentar dibawah... Terimakasih...
Semoga bermanfaat...