Hello Readers, I heard some of you are not getting out tutorials because u have no knowledge about Web hacking and you wanna learn web hacking .. So today i decided to write this tutorial for no0bs.
Because in this tutorial we are going to learn about IIS Web Hacking Exploit the Easiest way to hack for Noobs..
NOTE: THIS IS ONLY FOR EDUCATION PURPOSES, AND FOR SAFETY PURPOSE. WE ARE NOT RESPONSIBLE ANY HARM DONE BY YOU.
By using this Exploit an attacker can upload shell , Deface web site delete data etc. etc can do every thing without login..:D . Yeah you heard Right.. I know you all are getting exited, So lets's start :-
Note:- this is only for Windows XP users. For Windows 7 user , i will post soon ...
Follow the Instructions:-
1). First Of all we need to find Vulnerable site. Go to google and type the following dork:-
Dork- Intext:"Powered by IIS
Actually there is no particular dork be Creative use mind and create your own unique dork :) ..
If you are unable to find Don't worry ..See the end of the tutorial i have posted some sites :)
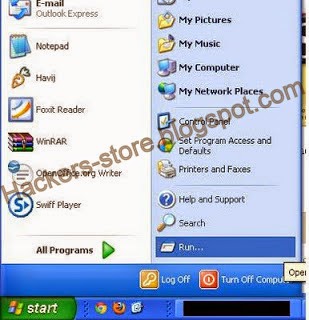
2). After Finding Vuln Site .Click on Start button And open "RUN"
3). Now type the following code in "RUN"
%WINDIR%\EXPLORER.EXE ,::{20D04FE0-3AEA-1069-A2D8-08002B30309D}\::{BDEADF00-C265-11d0-BCED-00A0C90AB50F}
4). Now a FOlder will open named "Web Folders"
Now Right Click in that folder then "New" And then "Web Folder"..
5). Now paste the url of the Vulnerable site And CLick Next..
6). Now it will ask you to give Name for that Web Folder leave as it is Click Finish..
Example : site.com/shell.php
Do the same to upload your deface also :D
Here are some site For Practicing ....
http://www.houtai123.cn/
http://news.rhvacnet.com/
http://israelshamir.net/
http://intellectual.members.easyspace.com/
http://hoodstarsports.com/
http://jennylo.co.uk/
http://hurrelvisualarts.com/
Soon i will post list of Vuln. sites of IIS Exploit/....