Hi all this is one of the popular attack know as browser auto pwn Vulnerability which we are going to use in this tutorial.
This is a simple vulnerability that allow attacker to hack to remote machine just by a single click by the victim.
NOTE: THIS IS ONLY FOR EDUCATION PURPOSES, AND FOR SAFETY PURPOSE. WE ARE NOT RESPONSIBLE ANY HARM DONE BY YOU.
-::Using Metasploit::-
In Metasploit there is a module known as browser autopwn. The basic idea behind that module is that it creates a web server in our local machine which will contain different kind of browser exploits. When the user will open the malicious link then the execution of the exploits will start against the browser of the user and if one of the exploits is successful a meterpreter session will open.
Follow these steps to carry out the attack :-
1). Open you backtrack/kali terminal make sure metasploit is there (which is present by default :D ).
2). Type #msfconsole on terminal
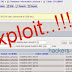
3). Now follow these steps as show in image
4). Use the browser_autopwn module
5).We have set up the LHOST with our IP address,the port to be 4445 and the URIPATH with / in order to prevent metasploit to set up random URL’s.now you will see below image.
Server started with 16 module.
6). Next we need to send the link to victim (like here http://192.168.205.131:8080/).as soon as the victim open the link its all done.
We have the meterpreter shell control in out hand you can do various activity you wish with meterpreter shell functionality.
Enjoy the hack of your victim machine have fun .!!!!
This is a simple vulnerability that allow attacker to hack to remote machine just by a single click by the victim.
NOTE: THIS IS ONLY FOR EDUCATION PURPOSES, AND FOR SAFETY PURPOSE. WE ARE NOT RESPONSIBLE ANY HARM DONE BY YOU.
-::Using Metasploit::-
In Metasploit there is a module known as browser autopwn. The basic idea behind that module is that it creates a web server in our local machine which will contain different kind of browser exploits. When the user will open the malicious link then the execution of the exploits will start against the browser of the user and if one of the exploits is successful a meterpreter session will open.
Follow these steps to carry out the attack :-
1). Open you backtrack/kali terminal make sure metasploit is there (which is present by default :D ).
2). Type #msfconsole on terminal
3). Now follow these steps as show in image
4). Use the browser_autopwn module
5).We have set up the LHOST with our IP address,the port to be 4445 and the URIPATH with / in order to prevent metasploit to set up random URL’s.now you will see below image.
Server started with 16 module.
6). Next we need to send the link to victim (like here http://192.168.205.131:8080/).as soon as the victim open the link its all done.
We have the meterpreter shell control in out hand you can do various activity you wish with meterpreter shell functionality.
Enjoy the hack of your victim machine have fun .!!!!













0 komentar